
|
Careers in Non-Profits |
Image |
Kayleigh Haskin |
|

|
Law Internship |
Image |
Kayleigh Haskin |
|

|
Law Internship |
Image |
Kayleigh Haskin |
|

|
GSU Teacher Residency |
Image |
Kayleigh Haskin |
|

|
Student-Led Listening IAC |
Image |
Kayleigh Haskin |
|

|
Starter Bikes |
Image |
Julia Faherty |
|

|
Brendan Saltaformaggio |
Image |
Georgia Parmelee |
|

|
Brendan Saltaformaggio |
Image |
Georgia Parmelee |
|

|
Prague Summer Schools |
Image |
Kayleigh Haskin |
|

|
Prague Summer Schools |
Image |
Kayleigh Haskin |
|

|
Prague Summer Schools |
Image |
Kayleigh Haskin |
|

|
Commercial Analysis Internship |
Image |
Kayleigh Haskin |
|

|
Personal Statement Bootcamp |
Image |
Kayleigh Haskin |
|

|
Liam's Legacy 2017 |
Image |
Kayleigh Haskin |
|

|
Great Powers and Global Peace |
Image |
amoore307 |
|

|
Tech Rec VR Adventures! |
Image |
jscott82 |
|

|
Toroidal structure2 |
Image |
John Toon |
|

|
Toroidal structure2 |
Image |
John Toon |
|

|
Toroidal structures |
Image |
John Toon |
|

|
Toroidal structures |
Image |
John Toon |
|

|
Alan Marco at TedX |
Video |
Steven Hodges |
|

|
Preparing hydrogel matrix materials |
Image |
John Toon |
|

|
Differentiating human intestinal organoids |
Image |
John Toon |
|

|
Hydrogel matrix containing intestinal cell clusters |
Image |
John Toon |
|

|
Alan Marco On Stage At TedX |
Image |
Steven Hodges |
|

|
German Day Event Photo 5 |
Image |
T. Jesse Brannen |
|

|
German Day Event Photo 4 |
Image |
T. Jesse Brannen |
|

|
German Day Event Photo 3 |
Image |
T. Jesse Brannen |
|

|
German Day Event Photo 2 |
Image |
T. Jesse Brannen |
|

|
German Day Event Photo 1 |
Image |
T. Jesse Brannen |
|

|
Changying “Charlie” Li |
Image |
Josie Giles |
|

|
TechSAge GVU posters |
Image |
Elena Gonzalez |
|

|
TechSAge GVU |
Image |
Elena Gonzalez |
|

|
All Eyez On Me Movie Poster |
Image |
nhansen7 |
|

|
The girl with all the gifts Movie Poster |
Image |
nhansen7 |
|

|
Buena Vista Soical Club: Adios Movie Poster |
Image |
nhansen7 |
|

|
Making Space Info. Flyer |
Image |
Ashlee Flinn |
|

|
The Babadook Movie Poster |
Image |
nhansen7 |
|

|
Racing Roots part 2 Drag Racing |
Image |
Jennifer Tomasino |
|

|
Racing Roots part 2 |
Image |
Jennifer Tomasino |
|

|
Raquel Lieberman |
Image |
Jerry Grillo |
|

|
Raquel Lieberman |
Image |
Jerry Grillo |
|

|
Tech in 60 Seconds: Homecoming Pomp and Circumstance |
Video |
Kristen Bailey |
|
|
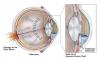
Glaucoma depiction BrightFocus Foundation |
Image |
Ben Brumfield |
|

|
The Goizueta Foundation Scholarships and Fellowships Annual Reception |
Image |
Annette Filliat |
|

|
The Goizueta Foundation Scholarships and Fellowships 10th Anniversary Celebration |
Image |
Annette Filliat |
|

|
Former Goizueta Fellows at GoSTEM’s Latino STEM Education Day |
Image |
Annette Filliat |
|

|
Pizza |
Image |
Kristen Bailey |
|

|
Pizza |
Image |
Kristen Bailey |
|

|
William Konop |
Image |
Renay San Miguel |
|